Common SAML user directory settings
This document describes settings that apply to all SAML based user directories:
- Active Directory Federation Service (AD FS)
- Security Assertion Markup Language (SAML)
- Suomi.fi
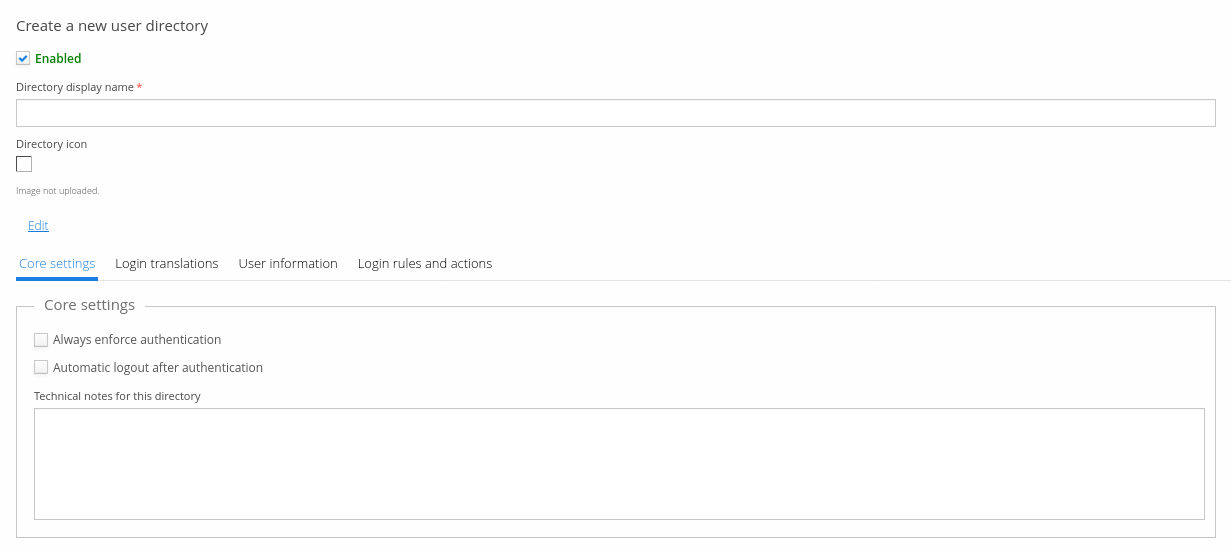
Core settings
Core settings consists of following settings.
- Always enforce authentication. This settings enables SAML-specific mechanism to enforce authentication. User must enter credentials even if he/she has existing authenticated session with the IdP. Please note that not all Identity Providers support this.
- Automatic logout after authentication. This setting was implemented because not all Identity Providers support enforced authentication. This setting ensures that user will be logged out of the SAML Identity Provider after every successful authentication.
- Technical notes are free-form notes relevant to configuring this user directory.
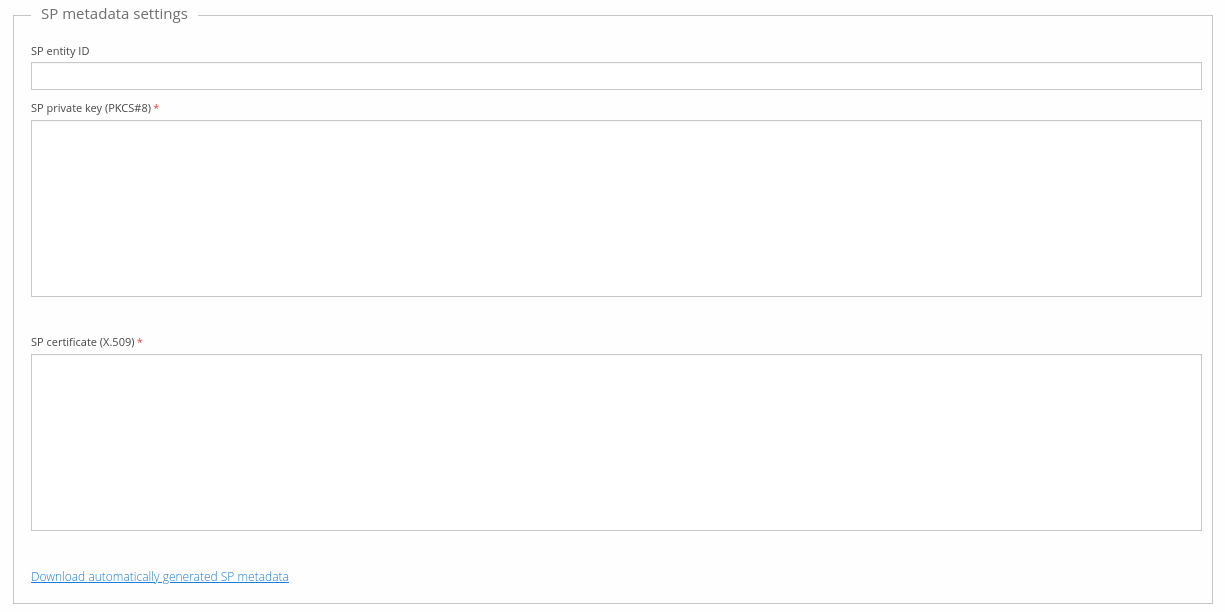
SP metadata settings
SP metadata settings consist of SP entity ID, private key and
certificate. For SP entity ID you can choose any random identifier if
you so choose, there are no requirements. Often, this identifier
includes the TrivoreID service URL and SAML authentication path. Example
value is https://<hostname>/saml/SSO.
TrivoreID does not place any restrictions either when choosing private key and certificate but the SAML IdP you are connecting to might have restrictions. Consult the appropriate person responsible for the IdP for any further information about these restrictions.
It is generally accepted practice to use self-signed certificates for SAML.
SP private key and SP certificate must both be in PEM format. Use any tool of your choice to generate self-signed certificate and private key. After you have configured all SP metadata settings, you can download automatically generated SP metadata.xml by clicking the link Download automatically generated SP metadata. You will need to import this xml file to the SAML IdP. You can make any changes to the xml file if needed as it is not cryptographically signed.
IdP settings
IdP settings consist of only single field where you can import the metadata XML file provided to you by the SAML IdP administrator. The XML file is structurally validated but testing is required to make sure everything works as expected.
User information
All user information described in Common user directory settings apply to SAML based user directories.
Additional SAML-specific user information is described in the table below.
Field | Description | Default value |
|---|---|---|
Legacy user mapping by username | Link users from user directory based on their username. This is a legacy option for backwards compatibility and should not be used on new user directories. This option is mutually exclusive with Link user with directory and Link ID fields. | False (not checked) |
Link user with directory | If true, link is made between existing Trivore ID user account and external user. This option is required if users are expected to this directory for sign-in instead of strong identification only. Strong identification use-case assumes that user is already logged in and therefore link is not required. | Depends on directory. ADFS and generic SAML directories have this enabled whereas Suomi.fi directory has this disabled as it is most commonly used for strong identification only. |
Use NameID based linking | Use SAML special attribute NameID as identifying attribute (Link ID). Enabling this option disables the Link ID field as these fields are mutually exclusive. Please note that it is possible to refer to this attribute in Link ID field with its name NameID too (which nowadays makes this field kind of redundant) | True (checked) |
Use NameID as username | Use SAML special attribute NameID as username. Enabling this option disables the username field as these fields are mutually exclusive. Username field is available only if manual username policy is selected. Please note that it is possible to refer to this attribute in Link ID field with its name NameID too (which nowadays makes this field kind of redundant) | False (not checked) |
Hash username with SHA-1 | Hashes username values using SHA-1 algorithm. Useful if username values contain sensitive information. | False (not checked) |