Configure Azure AD User Directory
Here you can find instructions how to configure TrivoreID authentication to work with Azure AD. Configuring Azure AD itself is out scope of this document (only general requirements provided here).
This configuration makes it possible to use existing Azure AD instance to sign-in to Trivore ID.
Configure Trivore ID
First, select User Directories from main menu as shown below and click button Add directory.
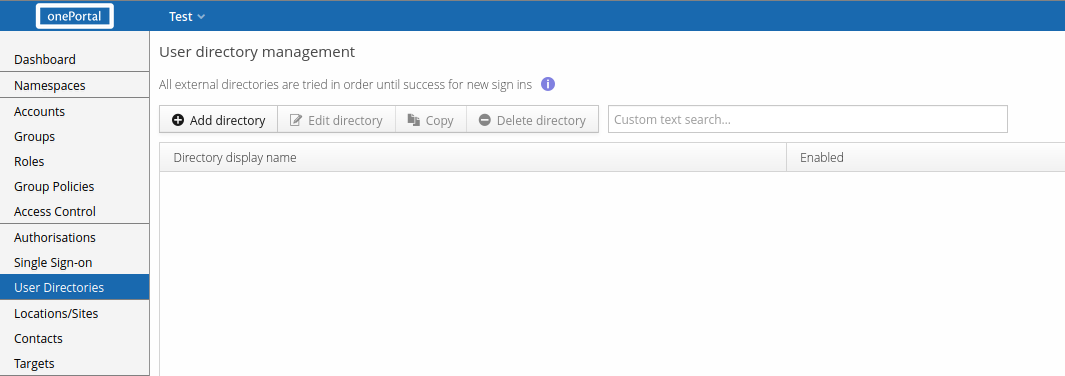
You will be asked to select directory type. Select Azure AD.
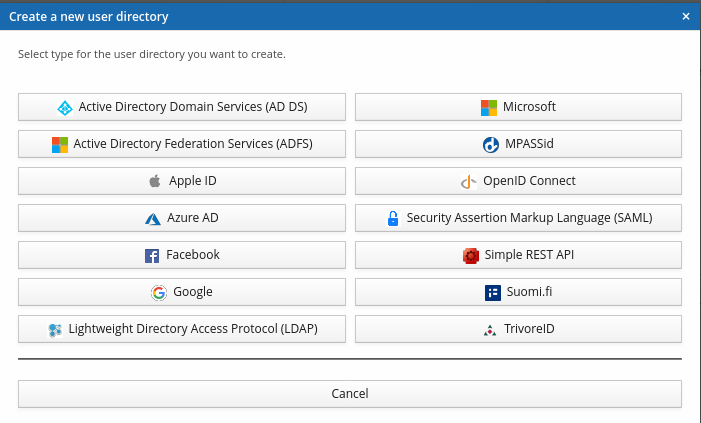
Core settings
Configure necessary settings, including Name, Tenant, Client ID and Client secret. Depending on your use-case, you may also need to adjust Scope value. Default Scope value provides Trivore ID access to basic user information on Azure AD, and is sufficient for most use-cases.
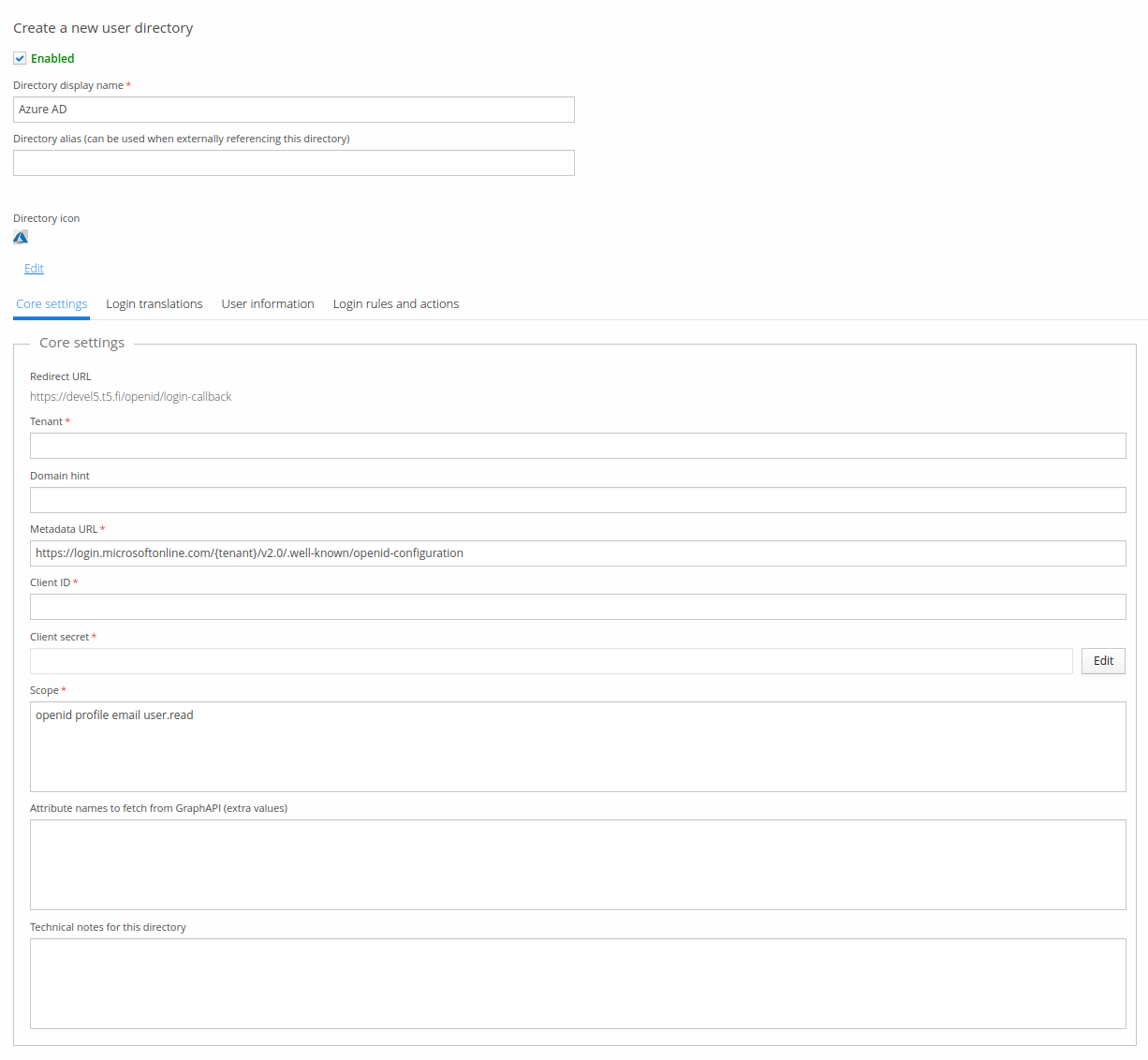
Appropriate values for Tenant, Client ID and Client secret all depend on the service provider (the organisation managing the Azure AD instance you are integrating to). Azure AD needs to be configured first before these values are available. You will need the Redirect URL (shown in picture) value when configuring Azure AD. Note that this value is different for every Trivore ID instance.
| Field | Description |
|---|---|
| Name | Any name you want to choose for this directory. |
| Tenant | Azure AD instance unique identifier. |
| Domain hint | Login domain hint. This field can be used to auto redirect user to on-premises ADFS if all users belong to a domain that should use it. refer to Microsoft documentation for more information. |
| Client ID | OpenID Connect client_id parameter. |
| Client secret | OpenID Connect client_secret parameter. |
| Scope | Adjust scope if needed. Scope defines what user information/attributes can be imported. Refer to Microsoft documentation for more information about appropriate Scope values. |
| Attribute names to fetch from GraphAPI (extra values) | Fetch these user attributes from GraphAPI on sign-in. This field is needed only on special cases where you have defined dot-separated mapping like “onPremisesExtensionAttributes.extensionAttribute12". In this case, field value should contain "onPremisesExtensionAttributes". |
User information
After you have configured necessary core settings, you may need to adjust user attribute mappings. Default mappings are suitable for most cases.
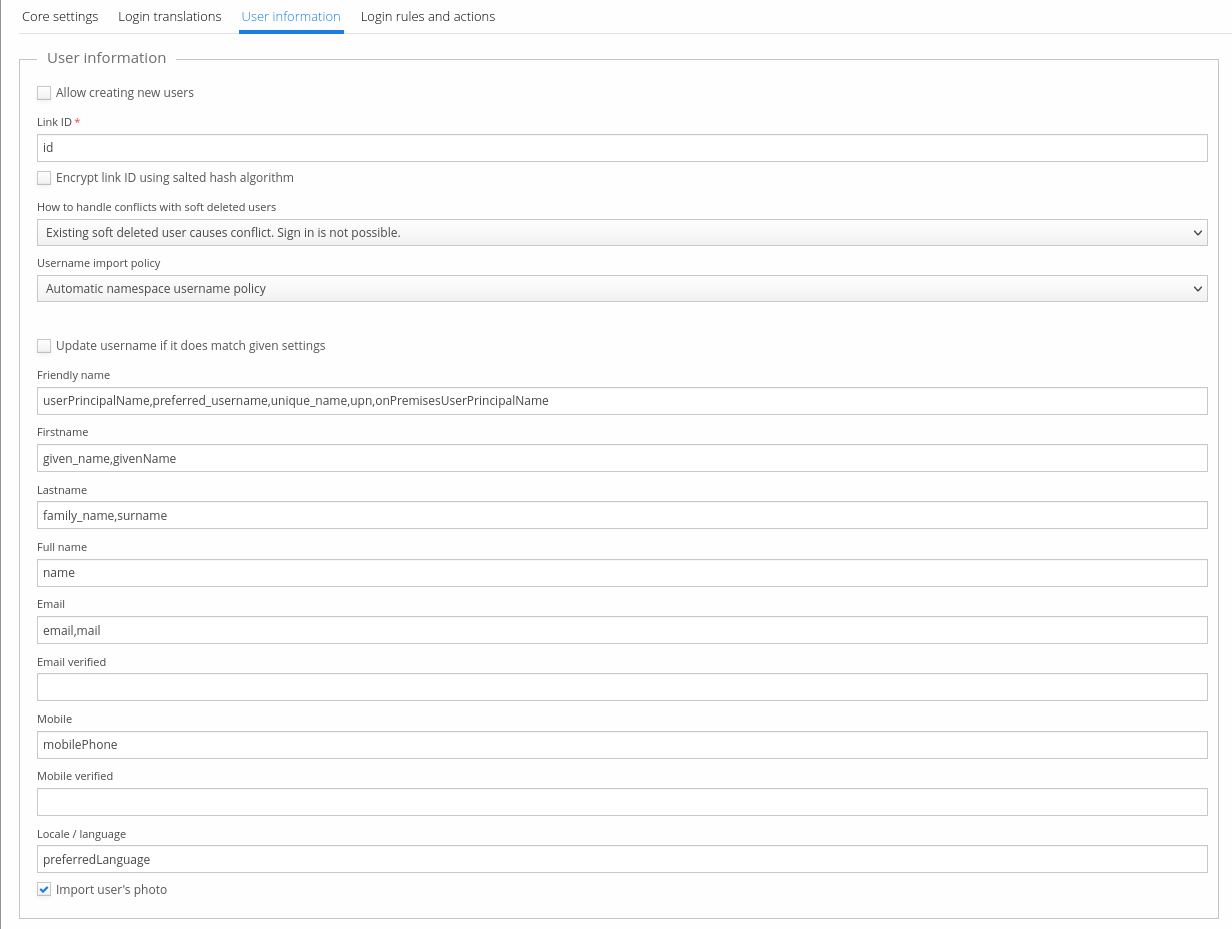
Azure AD uses common user attribute mappings documented at Common user directory settings.
| Field | Description | Default value |
|---|---|---|
| Import user’s photo | Import user’s profile photo from Azure AD. | True (checked) |
Group information
Azure AD uses common group attribute mappings, with some additions.
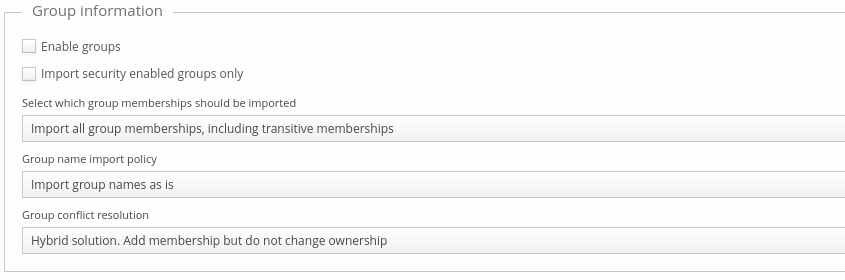
Below is table that describes Azure AD specific fields for group information.
| Field | Description | Default value |
|---|---|---|
| Import security enabled groups only | Import only security enabled groups from Azure AD (GraphAPI). For more information, see https://docs.microsoft.com/en-us/graph/api/resources/groups-overview?view=graph-rest-1.0 | false (not checked) |
| Select which group memberships to be imported | It is possible to import either direct group memberships only or all group memberships, including transitive memberships (ie. membership via another nested group) | Import all group memberships, including transitive memberships |