LDAP Server
LDAP Server is a built-in application in Trivore ID (Trivore Identity Service). For many organisations it is one of the major reasons to use Trivore ID. Then again, there are many organisations, which never need LDAP Server functionality.
LDAP Server functionality allows for organisations to use TIS as their
central user account and group repository and single point of
authentication for any supporting external service. The LDAP interface
is safe, as it is read-only and can only be used securely. It obeys the
security rules and policies defined in TIS. It is currently used for
authentication purposes only. LDAP Server must be separately enable for
each namespace in their own settings to enable this functionality. The
LDAP DIT root DN for each namespace is related to the namespace code of
each namespace. For example, if the namespace code is "company", the
root DN for that organisation will be o=company,cn=oneportal.
If your organisation does not currently use this functionality, please fee free to skip this chapter. Also ensure it is not enabled if it is not used. For those interested in more details on LDAP Server implementation, schemas, and internal structure, there is the document “onePortal™ Architecture and Functionality” (DocID 1001-111C). It is a technical guide available on request from support.
Enabling LDAP Server functionality in Web UI
LDAP Server must be enabled by Portal Admin for it to be available for any namespace. It is a prerequisite.
First select “System Preferences” on the Main Menu, and then in Platform section “Base settings” tab “Core”. This opens an important view shown in image below, where many important platform wide selections are made. These selections are normally made only once during or soon after deployment, and then left as is.
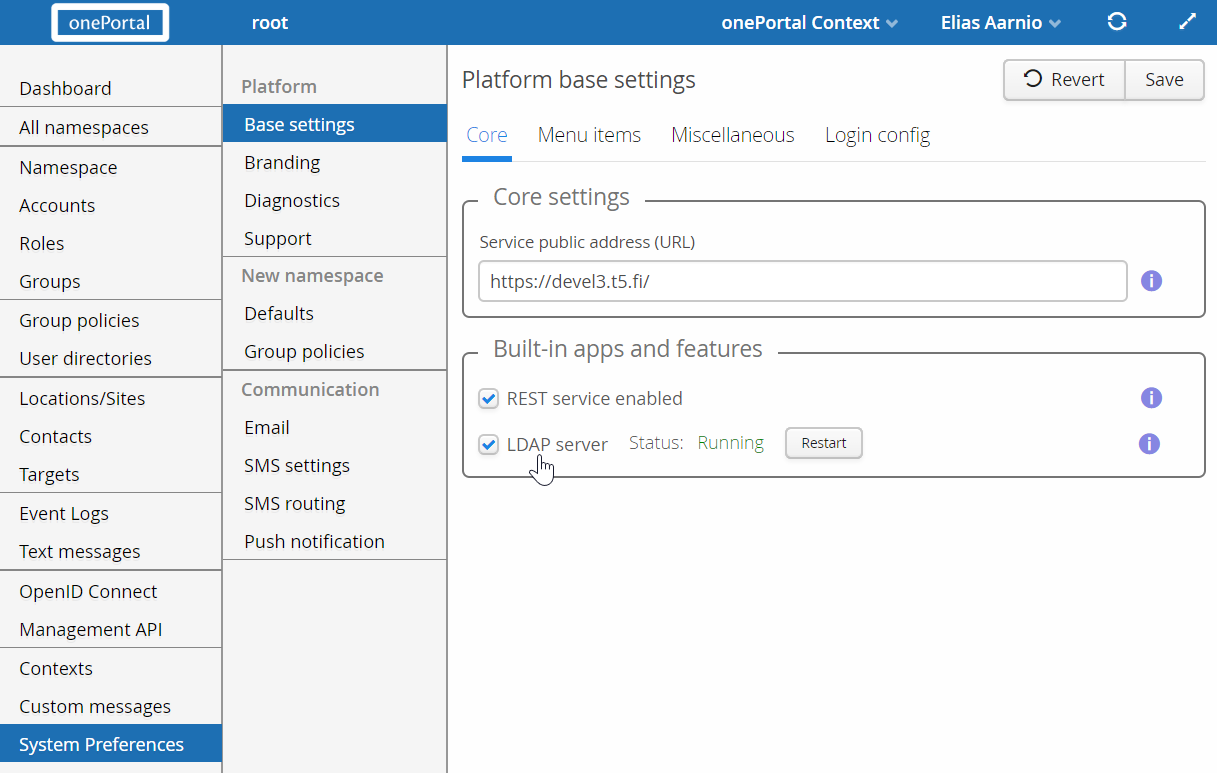
Select "LDAP Server" and then select "Save" to allow enabling LDAP Server at namespace level. Alternatively unselect it and select “Save” to disable LDAP Server platform wide. This setting can be considered as a “master switch” for the LDAP functionality. Depending on the business requirements, LDAP Server is generally either always disabled and it must not be enabled, or it is always enabled and widely utilised.
Portal Admin, please note, when the check box is unselected, the LDAP Server service is automatically stopped. This disables the LDAP service immediately for all namespaces. When it is selected, LDAP Server service is automatically started. The stopping and starting is done when the Save button is selected to save the configuration. The text next to LDAP Server shows the current state of LDAP Server.
This view can be used for checking the current state of LDAP Server and restarting it, shall it become necessary. Restart LDAP Server only after identifying a compelling reason to do it.
Enabling/disabling LDAP Server at namespace level
When LDAP Server is enabled at platform level, it is the responsibility of Namespace Admin to enable it for the namespace. To enable LDAP Server,
- Select “Namespace” on the Main Menu (see picture below),
- Open tab “Features”,
- Select “Enable LDAP Server for authentication”,
- Select “Save” to enable and activate LDAP Server for this namespace.
There are also two additional selections which are covered in the next section.
Disable operation is the same as enable, except instead of selecting, an unselect () is done before selecting “Save”.
Please note, it normally takes a while (from few seconds for namespaces with up to about 100 user accounts to up to few minutes for large complex namespaces with many groups) before LDAP authentication is fully available for external services and applications.
Operational considerations for each namespace
Picture below shows two additional settings, which are important for the operation and proper functionality of LDAP Server for a namespace.
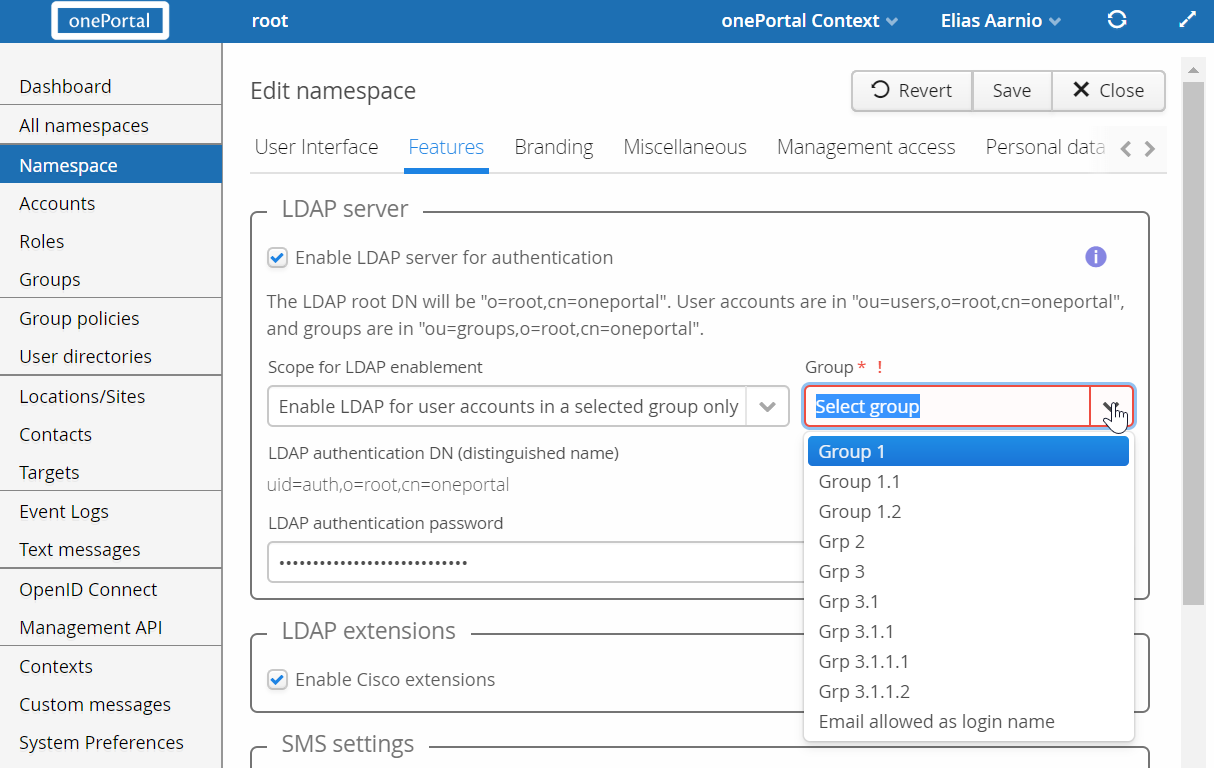
These two operative settings are:
- “Scope for LDAP enablement” setting determines which user accounts in the namespace will have LDAP enabled for them. By default it is enabled for all user accounts, but it is possible to select a group, and LDAP will be enabled only for user accounts directly or indirectly member of that group. If group limiting is made, it is recommended to use descriptive name for that group such as “LDAP_Auth_Enabled”.
- “LDAP authentication password” and its password. It is recommended to use very long password for this DN. Keep that password safe, and change it yearly or whenever organisation policy demands it to be changed. It is important to understand this DN does not allow any access to external services, neither is that DN able to make any changes to data in LDAP, or TIS. It is purely used as a technical “account” during the actual authentication.
“LDAP DN (distinguished name)” is generated automatically on TIS. LDAP DN is very commonly required by external services and applications for them to be able to use TIS for LDAP authentication.
When enabled and active, the LDAP server is available and accessible at the primary service address at TCP port 389 via StartTLS protocol and at TCP port 636 via TLS protocol. TIS is able to manage required TLS key and certificate. If external load-balancer is used, TLS is normally terminated there, and traffic is directed to TCP port 389.
For those interested, the LDAP Server TIS currently uses is OpenLDAP with tightened and optimised settings and full automation for TIS's purposes.